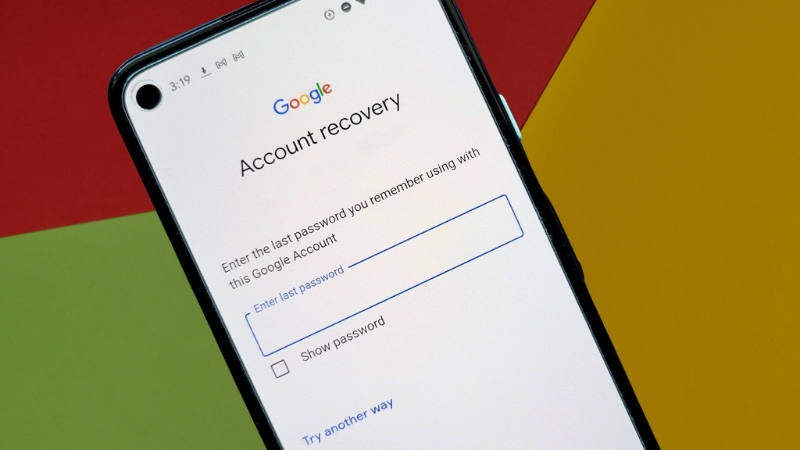
When standard recovery methods fail, Google account access is not lost by default, but recovery becomes slower, stricter, and evidence-based.
What helps in these cases is proving long-term ownership through technical signals such as device history, location consistency, prior passwords, and account usage patterns rather than relying on recovery emails or SMS codes.
Google does not reset accounts based on explanations or requests alone. It restores access only when its automated systems reach a confidence threshold that the person requesting access is the legitimate owner.
How Google Account Recovery Actually Works Behind the Scenes
Google account recovery is almost entirely automated. There is no general support agent who manually reviews cases or responds to explanations.
The recovery flow feeds answers into risk scoring systems originally built for fraud prevention, not customer service. These systems compare the recovery request against historical account signals collected over the years.
Google publicly confirmed this approach in multiple security whitepapers and blog posts following major account takeover waves between 2016 and 2020, when phishing and SIM swap attacks increased sharply.
Since then, recovery rules have become more conservative, favoring false negatives over false positives. In practice, this means legitimate users are sometimes locked out rather than risk granting access to an attacker.
The system evaluates three broad categories: historical consistency, technical environment, and behavioral continuity. Each failed recovery attempt reduces trust temporarily, especially if attempts are made from new locations or devices.
Why Recovery Emails and Phone Numbers Often Fail
Recovery emails and phone numbers are treated as convenience signals, not proof of ownership. They are frequently compromised in the same incidents that cause account lockouts.
Google internal security data shared at developer conferences shows that over 60 percent of account takeovers involve access to both the primary password and at least one recovery channel.
This is why entering a correct recovery email or phone number does not guarantee success. These signals only add weight if they align with other long-term indicators. If they do not, they are ignored.
The table below summarizes how Google weighs recovery factors.
Signal type
Importance level
Why it matters
Common failure reason
Recovery email
Low to medium
Secondary verification
Email also compromised
Recovery phone
Low to medium
SMS challenge
SIM swap or recycled number
Correct password
Medium
Knowledge-based proof
Password reused or leaked
Old passwords
High
Long-term ownership
The user cannot remember
Device history
Very high
Hardware fingerprint
New device used
Location history
Very high
Behavioral consistency
VPN or travel mismatch
Device History Is One of the Strongest Signals
The single most important factor when recovery options fail is device history. Google tracks device identifiers through cookies, hardware characteristics, operating system versions, and browser fingerprints. These signals are not stored as simple IDs but as probabilistic models of trusted environments.
Logging in from a previously used device significantly increases recovery success. In internal security presentations, Google has stated that recovery attempts from recognized devices are several times more likely to succeed than those from new ones, even if other answers are incomplete.
This is why recovery often works days later when retried from an old laptop or phone, even with the same answers.
If a device has not been used for months or years, its trust weight decreases but does not disappear entirely.
Location Consistency Matters More Than Accuracy
Contrary to popular belief, entering the exact city or address is not critical. What matters is consistency with past behavior. Google evaluates IP ranges, country-level location, and network type.
A recovery attempt from the same country and region as long-term usage carries far more weight than a technically accurate answer entered from a different location.
Using a VPN during recovery is one of the most common reasons for failure. VPNs introduce location volatility that closely resembles attack behavior.
The table below shows how location affects recovery scoring.
Recovery location
Trust impact
Explanation
Same city or region
Strong positive
Matches historical patterns
Same country, different region
Neutral to positive
Acceptable variance
Different country
Negative
High fraud similarity
VPN or proxy detected
Strong negative
Common attacker behavior
Prior Passwords Are More Valuable Than Current Ones
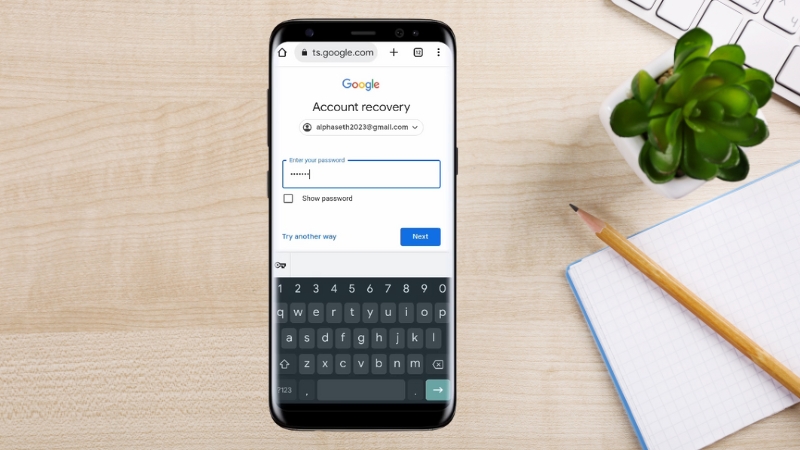
When the current password no longer works, entering old passwords becomes critical. Google explicitly states that older passwords are stronger proof of ownership than the most recent one.
This is because attackers often change passwords quickly after gaining access, while original owners can recall earlier credentials.
Even partial accuracy helps. Correctly entering a password from several years ago can outweigh multiple incorrect recent attempts.
Users who rely on password managers tend to perform better here, as managers often retain password history.
Time Delays Are Not Random
Many users experience a pattern where recovery fails repeatedly and then suddenly succeeds after several days. This is not a coincidence. Google intentionally enforces cooling periods after suspicious activity.
During these periods, the system waits for additional passive signals such as device reappearance, cookie regeneration, or login attempts from known environments.
Repeated submissions within short timeframes can reset this cooling period, delaying recovery further.
A simplified timeline looks like this.
Action
Effect
First failed recovery
Risk score increases
Multiple rapid retries
Additional restrictions
Waiting 48–72 hours
Risk score decays
Retry from a trusted device
Success probability increases
Why Explanations and Appeals Do Not Work

Google does not read free text explanations for consumer account recovery. There is no place to submit documents, identification, or personal stories.
This is intentional. Any system that allows human judgment at scale becomes exploitable.
This frustrates legitimate users but aligns with Google’s security model, which treats identity as a pattern of behavior rather than a narrative.
Business accounts underpaid enterprise plans have limited human escalation paths, but standard consumer accounts do not.
When Accounts Are Effectively Unrecoverable
Some accounts cannot be recovered. This usually happens when multiple factors align against the user: long inactivity, no trusted devices remaining, location mismatch, missing password history, and compromised recovery channels.
Google estimates, based on security research published between 2019 and 2022, that a small percentage of locked accounts are permanently inaccessible. This is considered an acceptable loss compared to the risk of unauthorized access.
Common irreversible scenarios include accounts created years ago and rarely used, accounts accessed only through public or shared devices, and accounts where all access occurred behind VPNs.
What Actually Helps When Everything Else Fails
@frankagency0 How to Recover Google Account Without Phone Number or Password | Guaranteed Method (2025) (1080p_30fps_H264-128kbit_AAC) #AccountRecovery #gmail #google #account #recovery ♬ original sound – 𝐅𝐑𝐀𝐍𝐊𝐀𝐆𝐄𝐍𝐂𝐘
When usual options fail, the only strategies that measurably help are technical and behavioral, not procedural. Use the same device, the same browser, the same network, and wait between attempts.
Enter old passwords even if unsure. Avoid VPNs completely. Accept that time itself is part of the process.
These are not tips in the motivational sense. They are behaviors aligned with how Google’s systems evaluate trust.
Final Perspective
Google account recovery is not designed to be forgiving. It is designed to be resistant to abuse on a global scale.
When recovery options fail, success depends on aligning with long-term signals that only genuine owners are likely to reproduce.